[HDCTF 2023]enc

打开进入这个函数
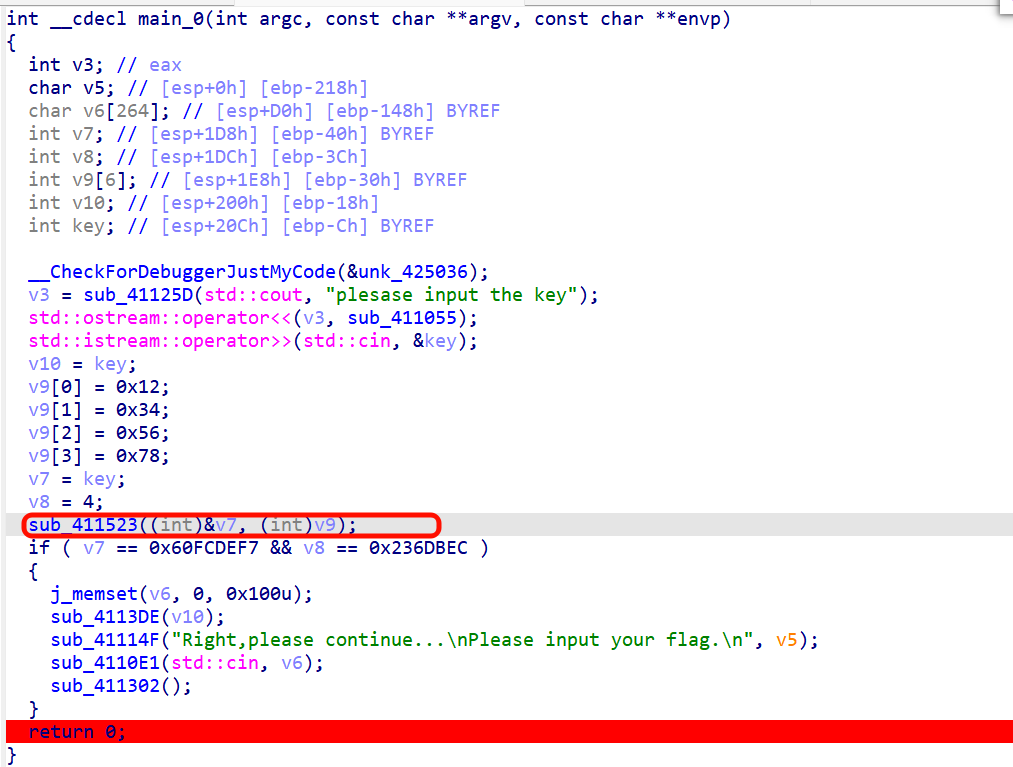
TEA
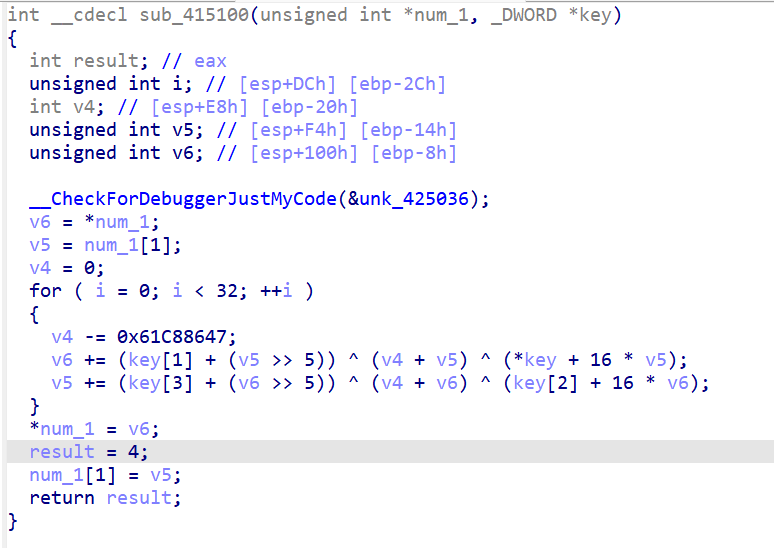
分析之后知道
下一步核对的v7和v8都是改变后的密文
v9才是密钥
解密时注意,异或的时候从后往前异或,倒着来
脚本
1 | #tea解密 |
SMC
继续看下面的函数
sub_4113DE —>sub_414C10—>sub_411046—>sub_414B00—>sub_411221—>sub_415340
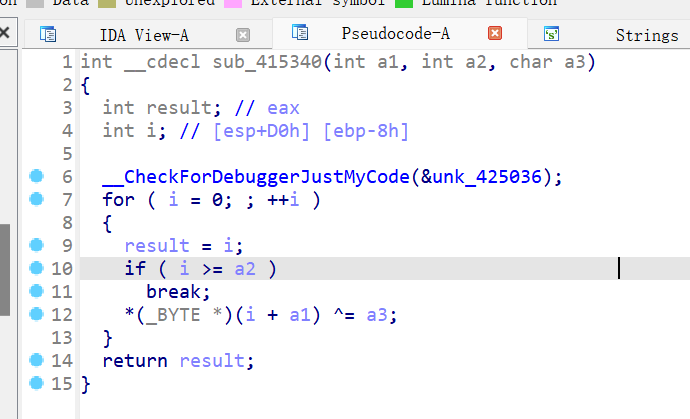
(char *)a1或(_BYTE *)a1是将整数地址a1转换为内存指针。- 然后通过
*ptr ^= a3修改该地址上的内容。
所以是SMC
那下一步就是找到它改变的地址的范围
打开x32xdbg
ctrl+g输入00415340
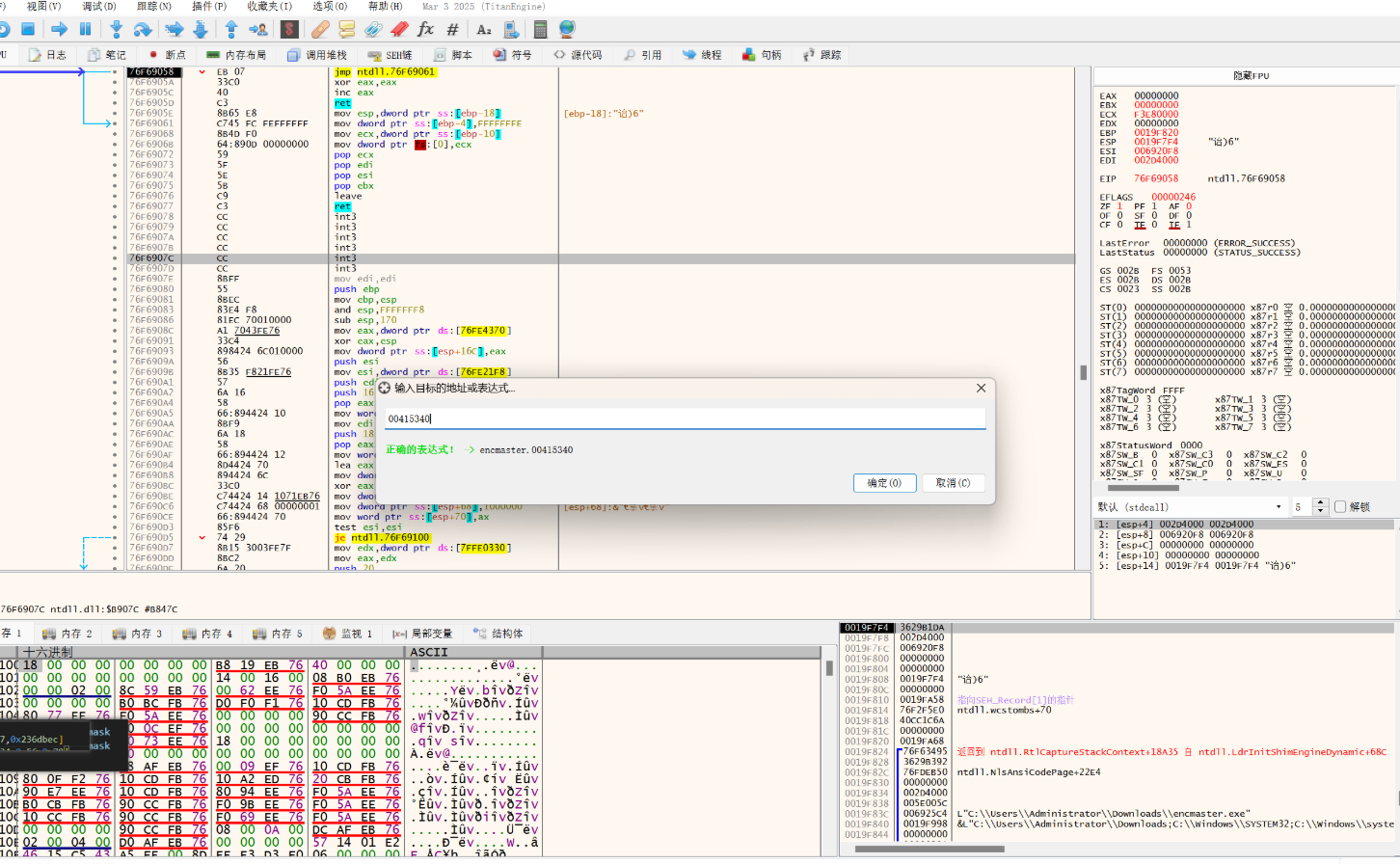
F9运行后会停在这里
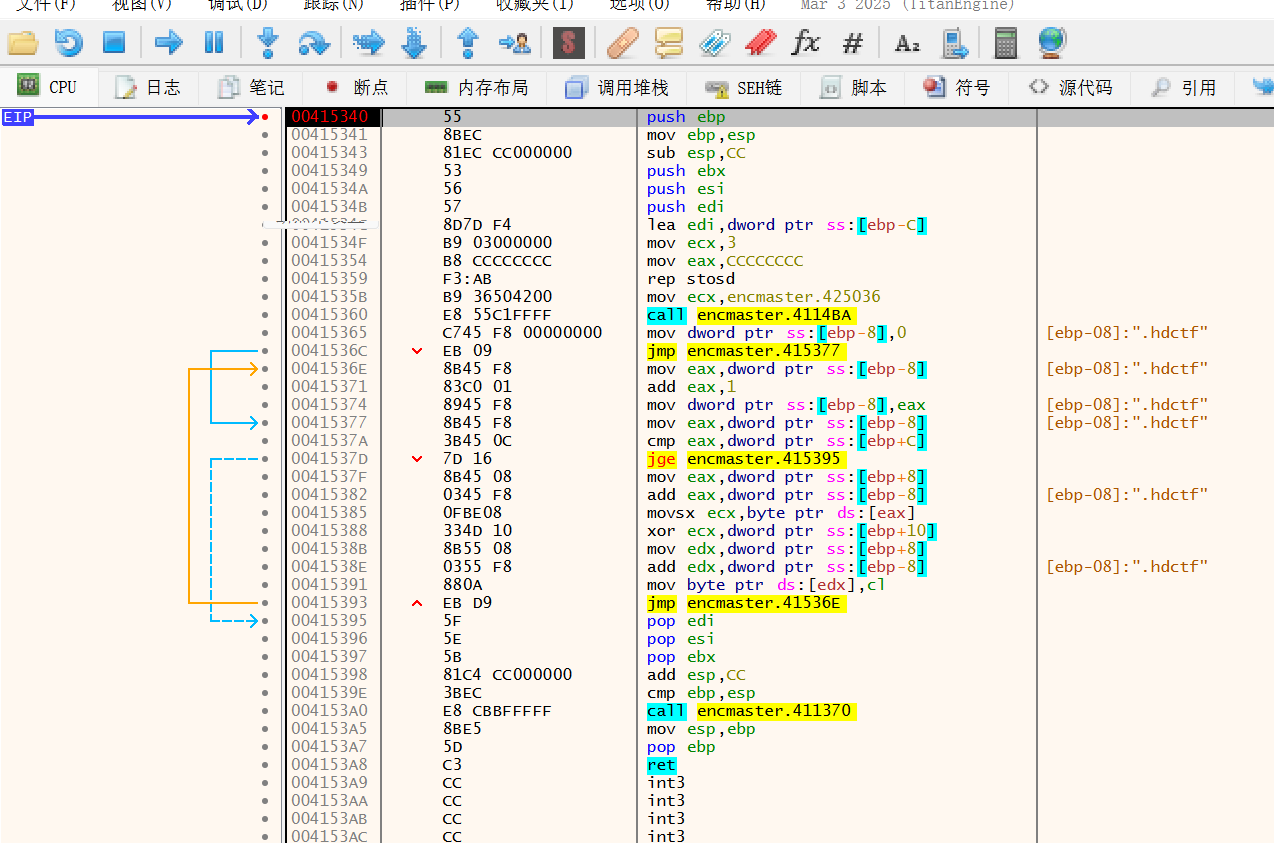
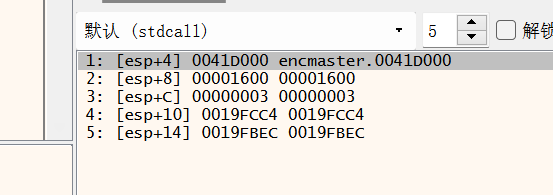
所以修改位置的位置头是0x0041D000
长度是0x600
所以在ida中运行脚本
脚本
1 | # 导入 ida_bytes 模块,这是现代 IDA Python 推荐的字节操作方式 |
之后再在函数头按U结构
再选中范围去C
就可以了
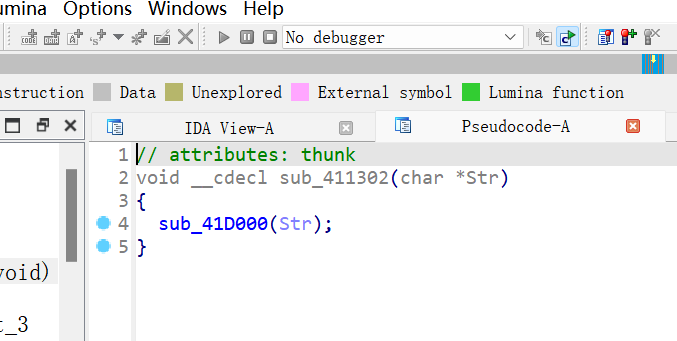
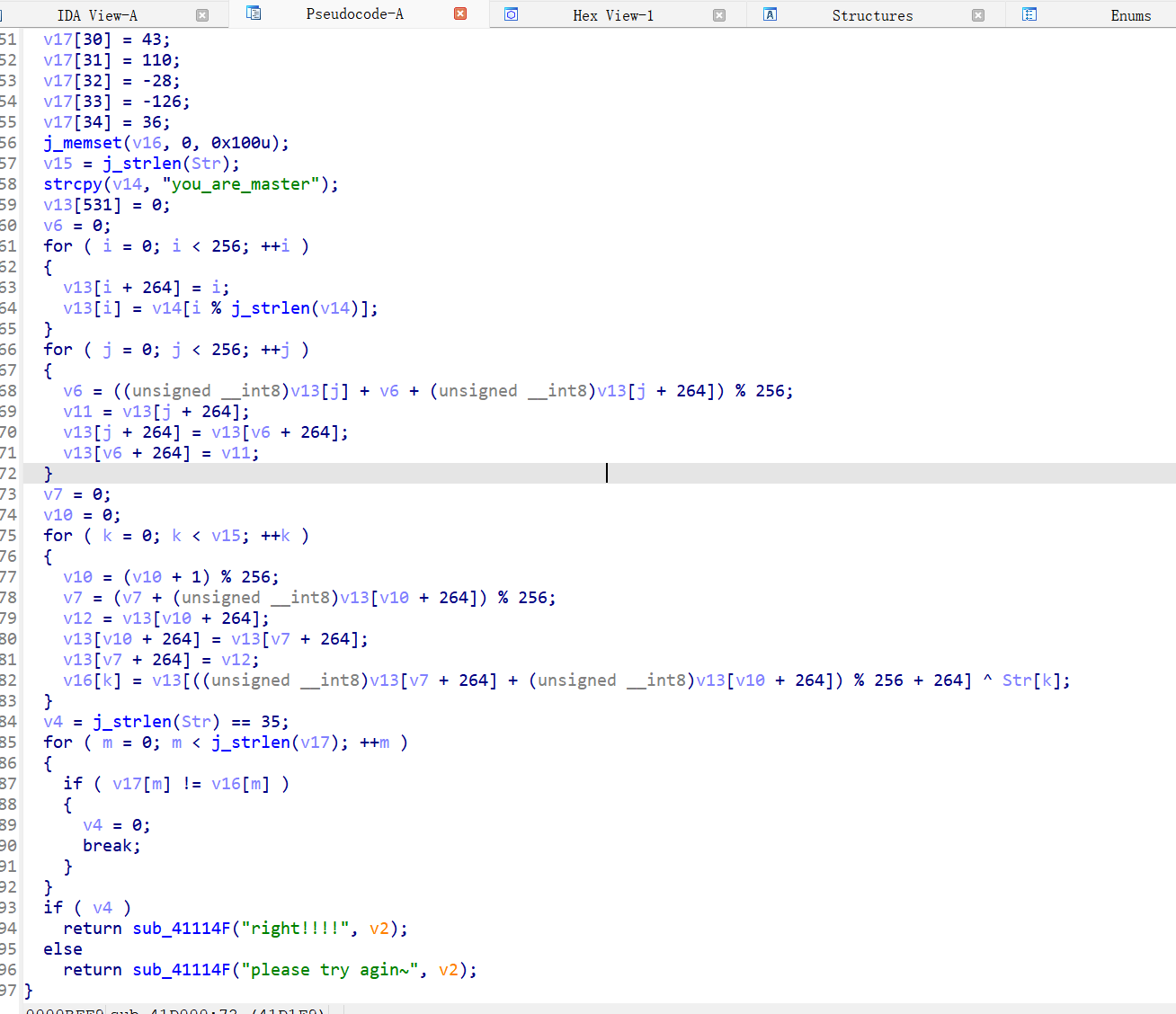
发现是RC4加密
脚本
1 | key=list('you_are_master') |
